iPads and iPhones are increasingly vital to the productivity of modern-day business operations. However, managing the security and compliance of a company-owned iOS fleet determines whether a device is an asset or a liability.
The best way to keep your organization's iOS devices secure is by remotely managing the behavior of these devices with configuration profiles through a robust management solution like SimpleMDM.
Whether you're an IT administrator looking to streamline operations or a business owner aiming to enhance device security, you can use SimpleMDM to deploy security-aimed configuration profiles like:
Software Update Policy for iOS
Passcode Policy
Certificate
VPN
Wireless Network
Extensible Single Sign-On
Web Content Filter
App Restrictions
We'll define these profiles and how a MacAdmin might use them to secure, control, and strengthen your devices, so there are no weak links in your hardware security. ⛓️
Software Update Policy for iOS
I always like to start with the best first! IMO, the best way to run a tight ship is to ensure all company-owned iOS devices meet the operating system minimum versions for compliance.
Tip: You can only deploy either a Major or Minor Software Update Configuration profile to a given endpoint at a time, not both. |
What it is
The Software Update Policy for iOS is a configuration profile administrators use to manage and control software update behaviors for an organization's iOS devices. Through this profile, administrators can define a variety of settings related to software updates, including:
The frequency of running updates.
What versions of software are acceptable.
When updates should be performed (e.g., during off-peak hours, specific times, etc.).
It's a tool that gives system administrators control over the update process on all Apple mobile devices within their organization, ensuring security, functionality, and consistency across the board.
Why it's used
By default, the Software Update Policy keeps machines within the accepted security and compliance parameters set by the system administrators, ensuring company-wide security and compatibility.
What it prevents
The Software Update Policy prevents users from running an endpoint on an older or incompatible OS outside organization-approved compliance standards.
Tip: Want to defer iOS updates? You can create a deferral of up to 90 days for Supervised iOS devices by creating a new Restrictions configuration profile and deploying it to iOS device types. |
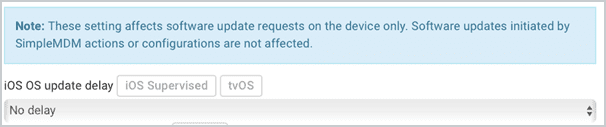
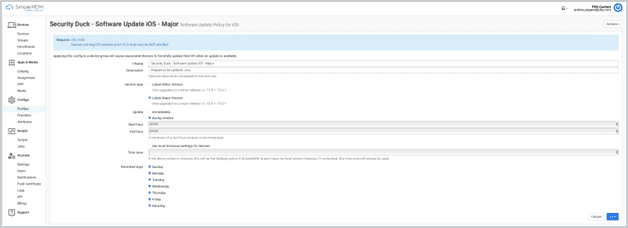
How Software Update Policy works in SimpleMDM
Choose to auto deploy either Major or Minor Updates.
Customize allowable days for updates to take place.
Choose to deploy immediately or in a specified duration window.
While this feature is excellent, we're about to see a DDM-supported facelift for updates that will blow your mind with capabilities! Stay tuned! 👀 |
Passcode Policy
A passcode policy is arguably the best way to keep your company's hardware and data safe if your machines fall into the wrong hands. 🙊
What it is
A Passcode Policy profile is a set of rules and guidelines determining how passcodes should be constructed and managed to secure devices or systems. These policies aim to enhance the security of devices by preventing unauthorized access. A passcode policy can dictate factors like:
Passcode length: The minimum or maximum number of characters the passcode must have.
Complexity: The combination of characters that should be included in the passcode, such as uppercase letters, lowercase letters, numbers, and special symbols.
Passcode expiry: The period after which the passcode must be changed.
Passcode history: The number of previous passcodes that cannot be reused.
Maximum attempts: The number of incorrect passcode input attempts allowed before an action is taken, such as locking the account or wiping the device.
Auto-lock and idle time: The length of inactivity before the device locks or resets itself.
The Passcode Policy configuration profile enables administrators to use the MDM to standardize, enforce, and manage passcode rules on an organization's Apple devices.
Why it's used
The Passcode Policy inherently forces users of the directed endpoints to set system passwords at a bare minimum set by the admin, not chosen by our *lazy* but lovely end users. This means you can set it and forget it, which makes enforcing SOC-2-type security and compliance standards across your org much more manageable.
What it prevents
This configuration profile protects sensitive company data from unauthorized access.
A passcode policy is like the quality of reinforcements around a medieval castle. Are you cool with a boring old water moat, or are we cranking up to a more secure lava moat? Is your wall made of puny pine wood or a solid, sturdy oak? 🏰 |
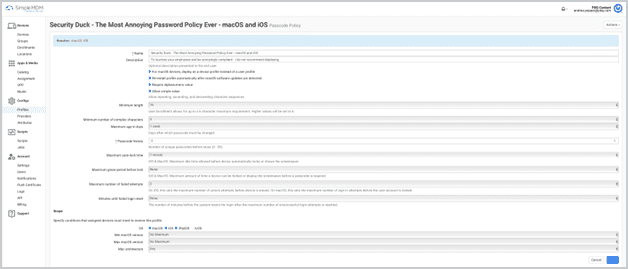
How Passcode Policy works in SimpleMDM
Specify the following:
Minimum length
Required alphanumeric value
Maximum password age
Number of unique passcodes before reuse
Auto-lock time
Allowed failed password attempts
Failed login reset parameters
Certificates
A Certificates configuration profile provides a secure and automated method for distributing and managing certificates on Apple devices to access corporate systems, apps, or networks.
What it is
A Certificates configuration profile is a configuration profile that embeds certificate or credential information into an Apple device.
Digital certificates are digital identities typically used to establish secure communications and authenticate the device or user to a network or service for Wi-Fi authentication and VPN access.
The system automatically installs the included certificates when a Certificates configuration profile deploys to a device. This means the user doesn't have to manage their certificates or know any associated security details.
There are several types of certificate profiles, including:
PKCS1: Contains just the certificate.
PKCS12: Includes both the certificate and the associated private key.
SCEP (Simple Certificate Enrollment Protocol): Allows certificates to be generated on demand from an SCEP server.
Why it's used
Two words: ease and security. The admin holds the master key (certificate). The admin can then use the MDM to take that approved key and mass deploy it to approved endpoints. It's like the admin holds the magic wand of approval and can easily grant that approval on a wide scale without compromising security.
What it prevents
Certificates prevent devices from accessing certain company assets without an authorized validation certificate.
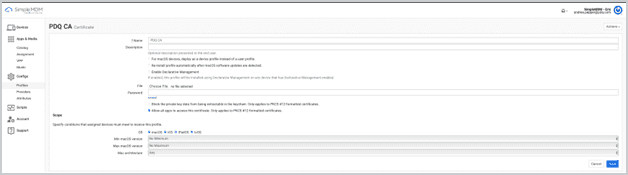
How Certificates work in SimpleMDM
Upload certificate file.
Configure credentials.
Configure PKCS #12 options if applicable.
VPN
VPN stands for virtual private network. It's a technology that creates a safe and encrypted connection over a less secure network.
VPNs work by routing your device's internet connection through your chosen VPN's private server rather than your internet service provider (ISP). This allows you to browse the internet using the VPN's secure connection.
What it is
A VPN configuration profile can remotely configure and manage virtual private network settings on an organization's iOS devices.
The VPN configuration profile enables administrators to control security protocols such as:
Connection type: This determines the protocol used for the VPN connection.
Server and remote ID: These details pertain to the VPN server's hostname or address.
Authentication type: This configures how users authenticate themselves to the VPN (e.g., password, certificate, or proxy credential).
Why it's used
This profile is used to mass deploy the VPN configuration settings. Administrators can preconfigure iOS devices to securely connect to the organization's VPN without requiring end users to set up the connection manually. This simplifies the user connection process and maintains secure access to the organization's network resources.
What it prevents
The VPN profile helps thwart cybercriminals looking to attack via shared network traffic!
A VPN encrypts your internet connection, hiding all the data you send and receive from prying eyes. This makes it significantly more challenging for threat actors to see what you're doing or steal your information.
Deploying a VPN configuration makes it easy for everyone in your organization to comply with a VPN product. Using a VPN on your organization's endpoints helps keep end users (especially the remote ones) safe in their network environment and prevents network attacks. In short, VPNs help to keep your company data private and secure. (And wow, do we love secure omg 💅)
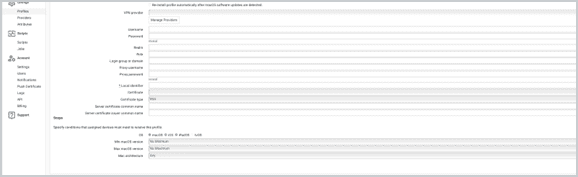
How VPN works in SimpleMDM
To add a Provider in SimpleMDM, navigate to Configs > Providers > Account Providers > VPN. |
Add provider.
Specify VPN configuration.
Specify VPN credentials.
Use custom attributes for attribute support during mass deployments.
Wireless Network
A Wi-Fi configuration profile is a preconfigured set of Wi-Fi network settings you can quickly push to your Apple devices.
What it is
The profile includes details such as:
Network name (SSID)
Network security type (e.g., WEP, WPA, WPA2, etc.)
Network password, if required
Auto-join settings
Proxy settings, if required
Once this profile is pushed to a device, it automatically knows how to connect to and manage its connection to the specified Wi-Fi networks. This enhances ease of use, and it simplifies the process of connecting many devices to a Wi-Fi network. It's precious in larger corporate, school, or institutional settings where many devices require access to the same Wi-Fi networks.
Why it's used
The Wireless Network profile is typically used to deploy the preset configuration settings for any approved Wi-Fi network, no matter how complicated. It takes the guesswork out of having users connect themselves and makes it easy to connect users automatically!
What it prevents
It prevents user error. (And, by definition, unauthorized network access.)
By leveraging the Wireless Network configuration profile, administrators can ensure a streamlined, secure, and hassle-free Wi-Fi connectivity experience for end users — removing manual setup processes and potential user errors.
Keep in mind: An internet connection is initially required for the maiden push deployment of this profile. |
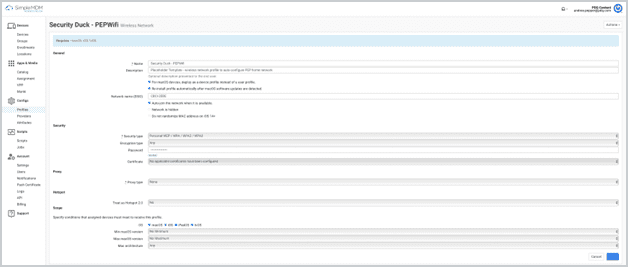
How Wireless Network works in SimpleMDM
Prereq: Cert profile (if applicable).
Choose security.
Choose encryptions.
Prefill network values and credentials.
Extensible Single Sign-On
The Extensible Single Sign On (ESSO) is a technology available on Apple devices that was introduced as part of the Apple MDM protocol. It's designed to provide a more unified and secure user experience.
What it is
The general concept of SSO is that once a user signs in to a platform, they can access multiple other applications or services without needing to authenticate (provide username and password) each time. With the Extensible SSO configuration profile, a user can authenticate once and gain access to multiple resources across apps and websites without logging in each time. This generates a configuration profile that includes identity provider (IdP) details, effectively creating a seamless sign-in process that can extend across various apps and systems.
It's "extensible" because it's flexible and not tied to any specific application or system. In recent iOS updates, the Extensible SSO supports protocols such as Kerberos and OAuth.
Why it's used
The ESSO behaves like a skeleton key. If a user wants to log in to multiple resources from the same IdP on the same endpoint, their credentials from the identity provider open all these doors.
Let's say you deployed ESSO for the Microsoft Office suite. In that case, once you initially log in to Word, the ESSO should bypass the need to log in separately for Excel or PowerPoint. Instead, it should automatically log you into these applications after the first successful credential authentication.
What it prevents
The ESSO profile is mostly so admins can be a lil' lazy. It prevents UE and manual errors by requiring less end-user input and relying more heavily on administrator automation.
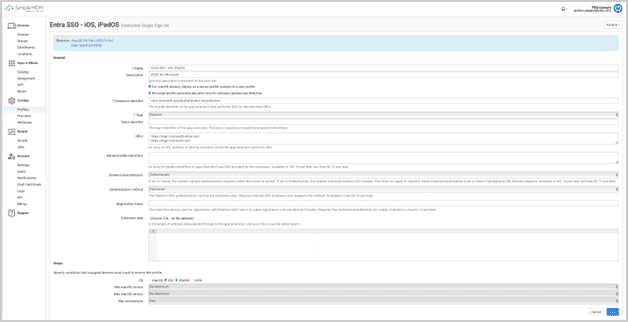
How Extensible Single Sign-On works in SimpleMDM
Specify the following:
IdP
URLs
Authentication method
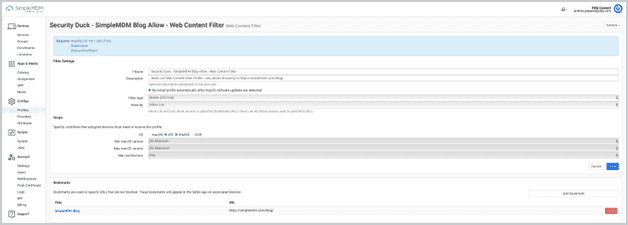
Web Content Filter
The Web Content Filter configuration profile allows network administrators to restrict or control the type of internet content Apple devices can access.
What it is
By leveraging a Web Content Filter, administrators can set restrictions on the internet content available on these devices. This makes the profile an excellent tool for educational institutions, businesses, or organizations looking to limit access to certain types of content.
The Web Content Filter configuration profile in SimpleMDM can allow or disallow specific URLs. This offers customizable levels of web access, letting admins choose between unrestricted access, banning several key websites, or allowing access only to specific websites.
Why it's used
This profile is usually an all-or-nothing approach. SMDM uses an allowlist or a denylist to customize security preferences around an endpoint's web content access. An admin can use a Web Content Filter to allow access to all sites except individually defined nonapproved websites.
For tip-top security, you can take the more extreme approach and denylist all sites, then individually list each website allowable for access on your endpoints. If you take this latter approach, prepare to set firm expectations with your end users (and possibly get upper management in your corner) because you will get tons of messages and tickets requesting access to sites outside of the approved list.
The drawbacks of this approach are:
It can add a lot of noise to the ticket queue, both for unnecessary sites and legitimate requests.
If we're being realistic, an end user may be tempted to take their work data to a non-org device without the same limitations.
This approach may, however, be highly ideal for a classroom environment.
Keep in mind: Whether you take an allowlist or denylist approach, these website lists are dynamic, and you can edit the Web Content Filter profile to include new sites at any time. |
What it prevents
This profile can prevent users from accessing non-secure sites.
How Web Content Filter works in SimpleMDM
Prereq: Supervision.
Specify an allowlist or denylist.
Add bookmarks to your list via URL.
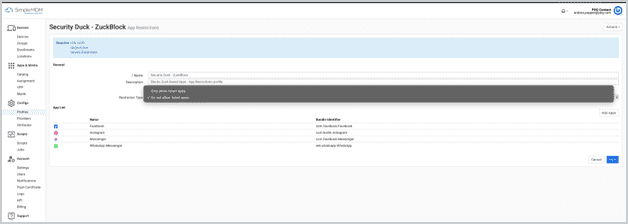
App Restrictions
The App Restrictions configuration profile is a tool administrators use to control or limit the usage of certain in-built and third-party apps on managed Apple devices.
What it is
An App Restrictions configuration profile allows administrators to remotely manage, limit, or prevent using specific apps on Apple devices in their network.
This has the same functionality as the Web Content Filter, but the administrator can restrict apps instead of limiting websites.
Why it's used
This profile allows administrators to control the app usage across all managed Apple devices, ensuring users engage with only the necessary and approved applications. This ultimately enhances productivity and maintains compliance with organizational policies.
What it prevents
This configuration prevents manual interference of application management from any source outside of the administrator.
How App Restrictions work in SimpleMDM
Pre-req: Supervision.
Specify an allowlist or denylist.
Search for applications via the regional App Store.
Search for listed applications via app name or bundle identifier.
Deploy these configuration profiles separately per device OS type for simple, secure, and comprehensive management in the future. |
Ready to take control of your company's iOS device security? Dive deeper into streamlined management with SimpleMDM. Start your 30-day free trial and experience the difference firsthand!