So you’ve heard the good news about the Platform SSO, and you’re ready to try it, huh?
Maybe you’ve already deployed the Extensible Single Sign-on configuration profile in the past, or perhaps you’ve even deployed the Microsoft Enterprise SSO.
Whatever the case, Platform SSO makes managing the Apple Hardware > Microsoft Software crossover much easier.
Let’s walk through how to configure Platform SSO.
PSSO in all forms is still in beta at the time of publishing. There are two versions:
Version 1: V1 is the first version of Platform SSO to roll out and is currently in use with Okta.
Version 2: V2 is in Public Preview with Entra ID. V2 supports more features than V1, like password syncing and user creation at login windows (although Microsoft doesn’t officially support groups at the time of publishing).
This Blog will only cover V2 deployment with Entra ID.
Platform Single Sign-on requirements
Before you configure Platform SSO, here are some nonstarters to consider.
Component requirements
macOS: Microsoft recommends using macOS 14 or later on target endpoints for the best experience with Entra and PSSO.
MDM Profile: Configure eSSO with associated domain payloads.
eSSO App Extension: The associated app needs to support PSSO and have domains listing all IdP URLs.
IdP PSSO Application: Use Company Portal version 5.2404.0 or later.
Install Company Portal on the device in /Applications path.
Company Portal does not need to be logged in.
Network requirements
The following minimum URLs must be allowed on your enterprise network for PSSO to function:
app-site-association.cdn-apple.com
app-site-association.networking.apple
sts.windows.net
login.partner.microsoftonline.cn
login.chinacloudapi.cn
login.microsoftonline.us
login-us.microsoftonline.com
config.edge.skype.com
Entra ID considerations
Ensure users are registered for Microsoft Entra multifactor authentication. Microsoft recommends using Microsoft Authenticator for the best experience.
For Google Chrome users, install and enable the Microsoft single sign-on extension.
Additional recommendations
Avoid deploying any MDM password restriction profiles alongside PSSO; instead, centralize all password configurations in Entra as the point of truth to avoid potential conflicts with MDM password restrictions.
Microsoft recommends deploying PSSO with conditional access MFA settings in Entra instead of per-user MFA.
Per Microsoft, PSSO is meant for cloud-based Entra, not Active Directory.
Set up the admin user on the endpoint before deploying PSSO; for best practices, exclude the local admin user from PSSO in the configuration.
Auto-deploy the Company Portal app so it hits the target endpoint ASAP; PSSO enrollment cannot proceed without its presence on the machine.
Protip: If it's a new machine, set up a local user using a federated Apple ID to speed up setup. To provision even faster, deploy an auto admin account through SimpleMDM.
1. Choose your authentication method
Choose your authentication method before setting up Platform SSO. When you configure your Extensible SSO profile (more on that in a minute), you need to select one of three authentication modes:
Password: This is the only way to sync passwords locally, as it syncs the user's Microsoft Entra ID password with the local account.
Secure Enclave: This system uses a secure enclave-backed, hardware-bound cryptographic key for Single Sign-on across apps using Microsoft Entra ID. It does not sync passwords locally.
Smart Card: This method uses an external smart card. Because it requires external hardware, we’ll focus instead on Password and Secure Enclave in this guide.
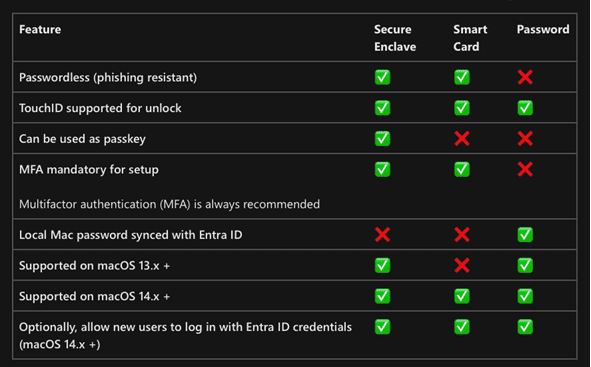
Refer to this authentication table provided by Microsoft to decide which deployment is suitable for your situation:
2. Create your Extensible Single Sign-On configuration profile
Deploy the Enterprise SSO plug-in
Follow the guidelines in Use the Microsoft Enterprise SSO plug-in on macOS devices. Deploy the Enterprise SSO plug-in.
To get my PSSO configurations, I followed the above guides where it shows the Other MDMs tab on the page and referencing settings on Configure Platform SSO for macOS devices in Microsoft Intune.
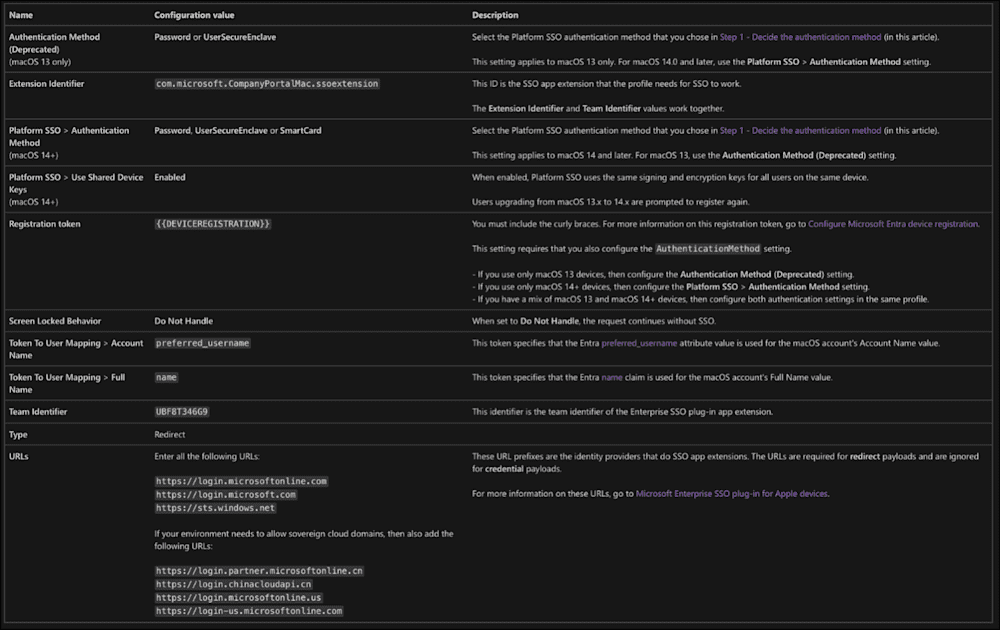
Create a PSSO Extensible SSO config profile in your MDM
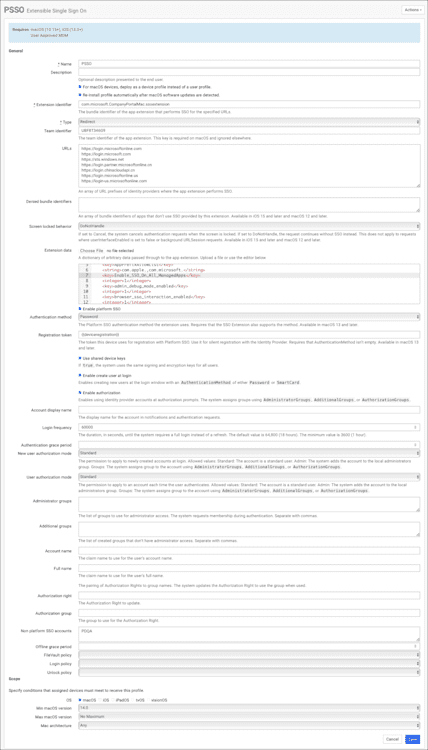
Next, you need to create your Extensible SSO configuration profile. Since we’re big fans of SimpleMDM, we'll walk through how to create this configuration profile in the product.
The following values are not set and will depend on your administration preference:
Authentication method
User authorization modes
Non-Platform SSO accounts
I've highlighted the most important values in this image.
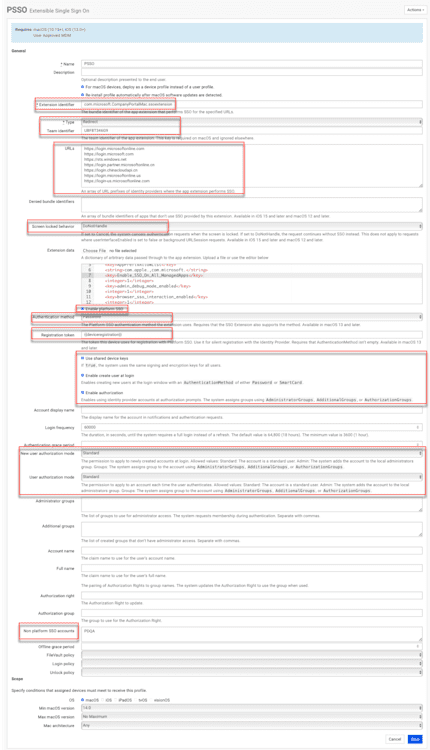
Go to Profiles > Create Profile> Extensible Single Sign-On.
Name your Profile.
Check the box For macOS devices, deploy as a device profile instead of a user profile.
Check the box to Re-install the Profile automatically after macOS software updates are detected.
Extension identifier: com.microsoft.CompanyPortalMac.ssoextension
Type: Redirect
Team identifier: UBF8T346G9
URLs:
https://login.microsoftonline.com
https://login.microsoft.com
https://sts.windows.net
https://login.partner.microsoftonline.cn
https://login.chinacloudapi.cn
https://login.microsoftonline.us
https://login-us.microsoftonline.com
Screen locked behavior: Do not handle
Check the box for Enable platform SSO.
Authentication method: Choose
password (local/Entra password sync) or
secure Enclave (higher security/ phishing resistant)
Registration token: {{deviceregistration}}
Check the box for Use shared device keys (this can prevent user creation if unchecked).
Check the box for Enable create user at login if you want to make new users from IdP credentials.
Check the box for Enable authorization.
Login frequency: 60000 (optional timeframe).
New user authorization mode: Choose Standard or Admin (I choose Standard).
User authorization mode: Choose Standard or Admin (I choose Standard).
Non-platform SSO accounts: (optional) Include the short name or full name of your IT admin user in this field to keep the local admin unbound from PSSO. For example, my IT Admin Account is PDQ Admin, so I listed its short name, PDQA, in this field.
Extension data: (optional)
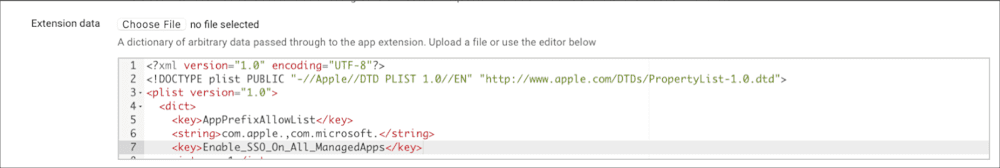
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>AppPrefixAllowList</key>
<string>com.apple.,com.microsoft.</string>
<key>Enable_SSO_On_All_ManagedApps</key>
<integer>1</integer>
<key>admin_debug_mode_enabled</key>
<integer>1</integer>
<key>browser_sso_interaction_enabled</key>
<integer>1</integer>
</dict>
</plist>
Here's a screenshot of what PSSO looks like configured in SimpleMDM:
For comparison, here's a Microsoft-provided example of what PSSO looks like configured in their MDM:
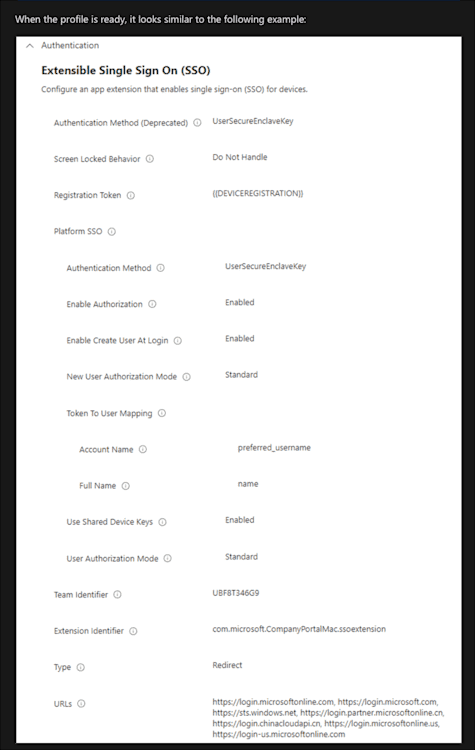
Both examples have a lot of crossover. Whether you're using SimpleMDM or another PSSO-enabled MDM, the fields covered in this blog should remain consistent.
3. Deploy Extensible Single Sign-on configuration profile
Now that you’ve made your Extensible SSO configuration profile, it's time to deploy it to your desired Mac group.
Loading...
4. Deploy the Microsoft Intune Company Portal for macOS deployment
Next, mass deploy the Microsoft Intune Company Portal for macOS deployment. I recommend deploying it as auto-deploy as opposed to self-service.
You can add this app from VPP in ABM or the shared Apps catalog in SimpleMDM. You can also download the Company Portal app for custom upload and mass deployment.
Protip: Double-check the target endpoint after app deployment to confirm that you see the company portal app in /Applications. PSSO registration does not pop up until this app installs on the machine.

Protip: You can open the SimpleMDM managed software update center on the endpoint computer to watch app installations and see when the Company Portal shows up.
5. Complete the macOS ESSO popup flow
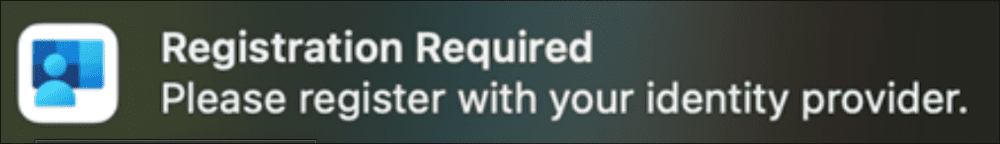
After the ESSO config is successfully pushed to the machine from the MDM and you see the Company Portal app present on the machine, you should see the Microsoft registration popup:
The notification should pop up every 15 minutes after the configuration installation.
If the popup isn't present:
You can log out and back into the user to trigger a popup.
You can go to System Settings > Users & Groups > Click Edit next to Network account server > Click Register next to Mac SSO Extension under Platform Single Sign-on.
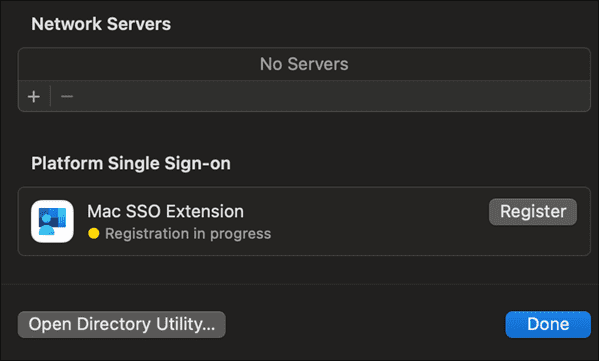
View the manual PSSO popup flow in action here:
Loading...
How to: Full flow examples
Password Authentication
Loading...
Secure Enclave Authentication
Loading...
Secure Enclave extra step
(As shown in the Scribe flow above.)
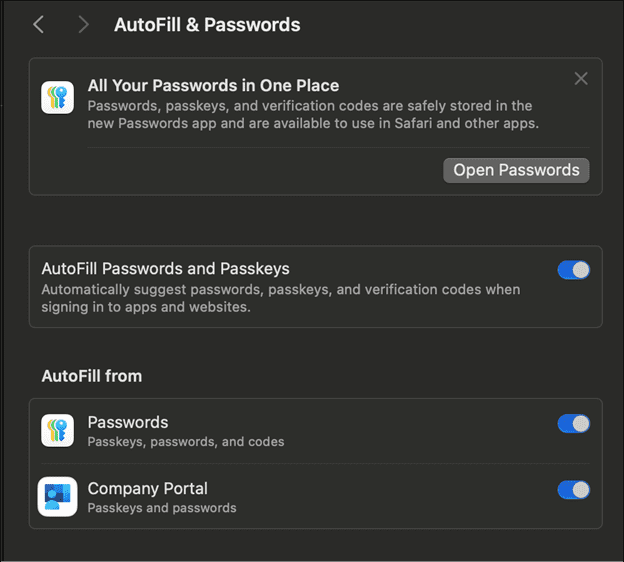
System Settings > General > Autofill & Passwords > Turn on the Company Portal passkey under Autofill from.
Common PSSO troubleshooting
If you encounter problems with your PSSO setup, there are a few resources you can turn to.
Microsoft macOS Platform single sign-on known issues and troubleshooting.
Run the following terminal command to check the PSSO State:
app-sso platform -sIf you use Secure Enclave auth, ensure the passkey setting is enabled in System Settings.
If you encounter issues, you may need to repair the PSSO connection in System Settings.
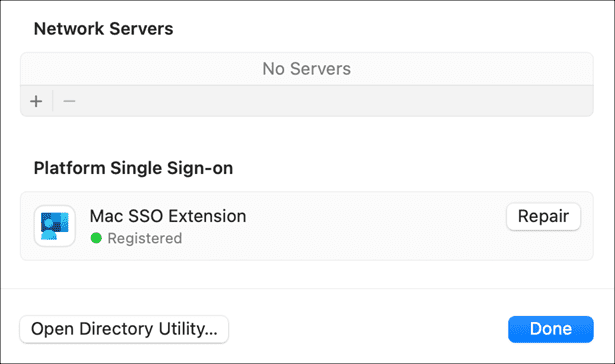
To re-establish the PSSO connection, go to System Settings > Users & Groups > Click Edit next to Network account server > click Repair.
You can also double check your on-prem network allowlist against Use Apple products on enterprise networks.
Test
To verify functionality, put the Single Sign-on to the test. After initial authenication, open a new private Safari window and visit https://portal.office.com/
After first logging in to https://portal.office.com/ using a standard Safari page or logging in to a Microsoft app like Outlook, you should be able to access other Microsoft domain sites without inputting your username and password again, even on private or incognito browser windows.
Platform SSO Resources
FAQ about Platform Single Sign-on
What is Platform SSO?
With Entra, Platform Single Sign-On (PSSO) allows your endpoints to authenticate into a Microsoft application once using your full password/Multifactor Authentication (MFA) process. After initial authentication, it automatically logs them into all other Microsoft domains.
Platform Single Sign-on is the evolved form of Extensible Single Sign-on MDM configuration file.
Apple's SSO extension facilitates integration with other products, using Entra ID as the identity provider and the Company Portal app as the broker.
Extensible SSO: With this adaptable protocol, apps support SSO via a third-party extension. This method offers the flexibility for an extension to handle authentication for multiple applications, which is beneficial for in-house or third-party applications lacking native iOS SSO compatibility.
Platform SSO: This protocol works at a device level, requiring only one configuration per device. It is more user-friendly, letting native and third-party applications use the same SSO credentials, including Kerberos and SAML-based authentication.
Is PSSO zero-touch deployment?
No, PSSO is not meant to make provisioning zero touch. By design, setting up a user account is still required for initial deployment.
Can PSSO create an initial user account on a Mac?
PSSO is not a method to create the first user on the machine. Before PSSO kicks in, it must be registered, requiring user interaction after enrollment and the login window.
Ready to simplify your macOS and Microsoft integration? Start your free trial with SimpleMDM today and experience seamless Platform Single Sign-On configuration.