As an IT professional, you're responsible for regularly receiving offboarded machines and swiftly turning them around to maintain a streamlined inventory. But sometimes you erase a Mac for reprovisioning only to see the dreaded Activation Lock screen pop up, asking for a prior employee's personal Apple ID email and password.
Activation Lock is Apple's built-in security feature that prevents third-party Activation if the device is lost or stolen. This feature locks your device, so restoring it or using EACS (Erase All Content and Settings) will not clear the lock.
Encountering this issue can be frustrating, but it might indicate the need to work smarter, not harder. Let's talk about how to work smarter with Activation Lock by setting it up to avoid those snags in the first place.
What is Activation Lock?
Activation Lock is a security measure for Apple devices designed to protect them. When the Find My iPhone (for iOS devices) or Find My Mac (for macOS devices) feature is enabled, Activation Lock requires the associated Apple ID and password to access the device. This additional layer of protection prevents unauthorized users from accessing the device, keeping your personal information secure.
For iOS devices, Activation Lock is automatically enabled when you turn on Find My iPhone.
For macOS devices (starting from macOS Catalina), Activation Lock works in conjunction with the Find My Mac feature and the Apple T2 Security Chip. When enabled, it offers protection similar to Activation Lock for iOS.
Activation Lock in enterprise environments
Activation Lock is an excellent feature for personal devices, but in enterprise environments, a locked-down machine can limit deployable devices for a sysadmin (talk about frustrating). And it can take a lot of work to unlock the machine: You might have to contact an ex-employee (regardless of their departure circumstances) and request their password to remove the lock. If that doesn't work, you may have to hit up your bestie in accounting to provide the hardware purchase receipt for that serial number to request Activation Lock removal from Apple Support.
Activation Lock vs. Find My
To add to the confusion, Find My and Activation Lock are not technically the same feature. Find My Mac is actually within the user interface. This is separate from Activation Lock, which works in the background to prevent devices from accessing activation servers and being usable after a system restore.
Find My: Find My macOS has features that help you proactively locate, lock, or erase your device. Find My macOS needs to be manually enabled within System Settings > iCloud. This feature is compatible with Macs running macOS 10.7.5 or later.
Activation Lock: Activation Lock is a security feature designed to protect Apple iOS 7+ devices and Macs with Apple T2 Security Chip or later. Activation Lock operates at a system level, making it difficult for unauthorized users to erase and reactivate your device. When Activation Lock is enabled, the user's Apple ID and password are required to:
Turn off Find My on the device.
Erase the device.
Reactivate and use the device.
System requirements for Activation Lock include 2018+ Macs with Apple T2 Security Chip or later and running macOS Catalina or later.
Types of Activation Lock
According to Apple Platform Deployment documentation, two types of Activation Lock are available for enterprise use: Organization-linked and User-linked Activation Lock.
Organization-linked Activation Locks offer greater control to organizations and are exclusively enabled via MDM, while user-linked Activation Locks allow individual users more control since they are enabled by the user via their personal iCloud account.
Should you enable Activation Lock for your fleet?
If you are not intentional about managing your Activation Lock and Find My features for your users, it will become a gigantic pain in your wallet. Mismanagement can turn a $3K engineering spec into parts or even a paperweight, consuming time and resources.
You may be yelling at me from your side of the screen: "But Pepper, I use managed Apple IDs for our organization! There's no 'Find My' feature when using managed Apple IDs... so I should be good, yeah?"
Not necessarily.
While it's true that a managed Apple ID account type does not have a Find My option, using a managed Apple ID alone does not keep the machine itself from being locked.
For example, without further configuration from the admin, there is nothing to keep the user from logging out of the Managed Apple ID and logging back into iCloud with a personal iCloud account. In this scenario, your enterprise device is now activated locked with an individual iCloud account to which you do not have the password.
Perhaps you protest again, "But Pepper, if I turn off Find My, I won't be able to track my machines! And if I disable Activation Lock, what is to prevent my users from taking the machine?"
Girl, you're right, but the pain of dealing with locks can sometimes outweigh the benefits. Additionally, other applications can help solve that issue.
Here are a few other tracking options:
iOS: SimpleMDM can auto-deploy the SMDM app that provides location tracking.
iOS: MDM Lost Mode: (requires supervision) Lost Mode can lock devices with custom messages and act as a replacement for Find My iPhone/iPad.
Also, some cloud-based backup services and endpoint protectors you may already use have location tracking built in.
And to your second point, clever admin, remember that through an MDM like SimpleMDM, you can lock down the machine at any moment, making it impossible for the user to continue using it without the lock code. They could keep the device but, again, paperweight.
How to manage Activation Lock via Apple Business Manager
Let's take it all the way back... to Apple Business Manager. As of WWDC 2024, Apple introduced the ability to disable Actication Lock at the ABM level. Apple Business Manager users with Manage Device privileges can now turn off Activation Lock for organization-owned devices before they reach MDM. This feature supports iPhone, iPad, Mac, Apple Watch, and Vision Pro. Click through the Scribe below to see where to find this feature in Apple Business Manager:
Loading...
How to manage Activation Lock via SimpleMDM
There are a few ways to manage Activation Lock with SimpleMDM. But first, make sure your devices are supervised or auto-enrolled. In Mac management, your efforts to control system restrictions will go much smoother if you deal only with supervised/auto-enrolled devices. If this doesn't reflect your current inventory, you should aim to achieve a supervised configuration as you build up your MDM architecture.
Here are the commands and keys that I go over in this blog that you'll want to write down: Activation Lock Mode (ActivationLockAllowedWhileSupervised) iOS and macOS: This MDM command manages Activation Lock at the MDM level. Disable Find My (DisableFMMiCloudSetting) macOS: This key is designed to disable the Find My functionality in iCloud Settings. To disable the user interface functionality of Find My Mac, supplement the ActivationLockAllowedWhileSupervised command with DisableFMMiCloudSetting, deployed as a custom configuration profile via MDM as "true" to your desired Mac computers. iOS Account Modification (allowAccountModification) iOS: This key is designed to control user account modification. Deploy it as a restrictions profile via MDM as "false" to prevent further user-level account modification. |
Activation Lock Mode (macOS and iOS — requires supervision)
ActivationLockAllowedWhileSupervised is an MDM configuration command that dictates whether the Activation Lock feature is allowed on supervised devices within the organization.
If you're lucky enough to be a MacAdmin with a fully supervised inventory, checking the status of this key command should always be the highest priority in your configuration hierarchy. This command is the crown jewel of simplification.
Activation Lock Mode drop-down options on SimpleMDM: Disable = This option prevents the user from enabling Activation Lock. Enable = This option enables MDM Activation Lock on an organizational level. User Enabled = This option does nothing from the MDM side and allows users to enable manually. |
What happens when Activation Lock Mode is enabled
You avoid a race condition scenario by setting Activation Lock Mode (ActivationLockAllowedWhileSupervised) to enabled (true). If the MDM enables first, it can disable the lock from that point forward as long as it maintains enrollment. If the user enables it first, they must then be the one to disable it before MDM can take over management. Setting the mode to enable it during initial Automated Enrollment (e.g., newly purchased devices) ensures MDM's activation takes precedence, allowing easy lock deactivation and streamlined management. This can be ideal for admins confident that their present and future fleets are 100% auto-enrolled.
What happens when Activation Lock is disabled
If you set the Activation Lock Mode (ActivationLockAllowedWhileSupervised) command to disabled (false), supervised devices cannot enable the Activation Lock feature.
This applies to devices at the time of enrollment. To check that it is set up correctly in SimpleMDM, do the following steps:
Under 'Devices' in the sidebar > click Enrollments > click the Settings tab on that page.
Make sure Activation Lock Mode is set to Disable.
Loading...
And there you go! From this point forward, all supervised devices with no prior activation associations cannot be locked on an activation server level.
It's important to note that this setting will not change the behavior or user interface of Find My.
That means this setting being disabled looks exactly the same on the endpoint as when the setting is enabled. Here are a few considerations to note:
There's no way to test in the user to confirm that this is functioning as intended outside of a "test" erase.
The user can still log in to Find My, which creates user-level permission restrictions within the operating system if you attempt to use Erase All Content and Settings.
To supplement this command for ease of administration, I recommend another macOS key: DisableFMMiCloudSetting.
DisableFMMiCloudSetting (macOS)
When applied, the DisableFMMiCloudSetting macOS key disables the Find My Mac (FMM) settings in the iCloud preferences on the target macOS devices.
This key command differs from the first in that it gives you the gratification of changing the user interface when enabled and being more cooperative with manually enrolled devices and auto enrollments. When this command is enabled and deployed as a restrictions profile, the Find My pane in macOS becomes greyed out.
The DisableFMMiCloudSetting key does not explicitly require device supervision, but it does need to be deployed to the target macOS devices through an MDM configuration profile containing this payload.
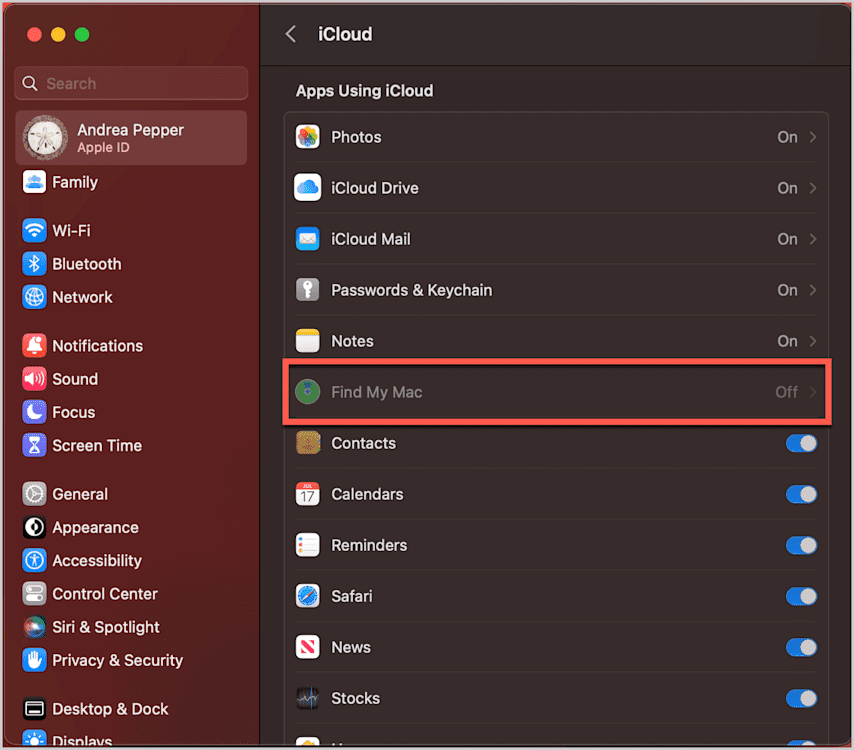
Here's how to use this command in SimpleMDM:
1. Go to Configs > click Profiles > click Create Profile > select Custom Configuration Profile
Loading...
2. Add the following payload as new custom configurations.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDisplayName</key>
<string>Restrictions</string>
<key>PayloadIdentifier</key>
<string>com.apple.applicationaccess.67A8AB6B-A67B-4193-8681-FA78886B143D</string>
<key>PayloadType</key>
<string>com.apple.applicationaccess</string>
<key>PayloadUUID</key>
<string>67A8AB6B-A67B-4193-8681-FA78886B143D</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>allowAccountModification</key>
<false/>
<key>allowFindMyDevice</key>
<false/>
<key>allowFindMyFriends</key>
<false/>
</dict>
</array>
<key>PayloadDescription</key>
<string>ios account settings restriction profile not managable </string>
<key>PayloadDisplayName</key>
<string>Disable modification of IOS account settings </string>
<key>PayloadIdentifier</key>
<string>com.accountsettingsmodify.disabled</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>E08E9953-CA91-4924-9F85-8D90CFAE9C41</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>Note: This profile can be created via iMazing profile editor from scratch if needed.
allowAccountModification (iOS – requires supervision)
Unlike DisableFMMiCloudSetting, iOS devices do not have a specific key command to disable the Find My interface and address related user-level restrictions. The closest option would be the allowAccountModification command key set to false and deployed as a restrictions profile.
The allowAccountModification command controls whether users can create, modify, or delete iCloud, Mail, Calendar, and other accounts on their devices.
When this command is set to true, users can add, modify, or remove accounts on their devices for services like iCloud, Mail, and Calendar. If set to false, the command restricts users from making account modifications, effectively locking the current account setup on the device.
Be very cautious before using this command. It will freeze all accounts in place and can only be changed once the profile is lifted. This command would be ideal for brand-new devices, devices where no accounts are desired, or devices with configured email, CalDAV, CardDAV, VPN, etc., accounts already deployed via MDM.
Here's how to use this command in SimpleMDM:
1. Go to Configs > click Profiles > click Create Profile > click Restrictions Profile > unselect Allow account modification.
Loading...
Note: Apple announced during publication that the allowAccountModification key will also be available for Mac deployment with the release of macOS 14.
Activation Lock FAQ
What's the difference between Activation Lock's commercial deployment vs. organizational deployment?
Activation Lock for organizational deployment is not the same beast as commercial deployment. Commercially deployed Activation Locks suit individual users who manually manage their devices without a centralized system. In contrast, organizationally deployed Activation Locks employ centralized management through MDM solutions for better device control.
What are the system requirements for Activation Lock?
According to Apple, Mac computers require Apple silicon or the Apple T2 Security Chip to be eligible for Activation Lock. Machines 2017 and earlier are still eligible for Find My Mac lock. If an eligible Mac computer uses Device Enrollment and is upgraded to macOS 10.15 or later, Activation Lock is disallowed by default and can optionally be allowed. Managing Activation Lock on installations (not upgrades) of macOS 10.15 or later requires the device to be supervised.
What are some troubleshooting tips for Activation Lock?
Here are a few troubleshooting tips from Apple that I wish I had known sooner when managing Activation Lock.
"Suppose that your MDM solution is unsuccessful in removing Activation Lock. Then, on the Activation Lock Screen, enter the user name and password of the account that created the device enrollment token that links the MDM solution to Apple School Manager, Apple Business Manager, or Apple Business Essentials. This is an account with the role of Administrator, Site Manager (Apple School Manager only), or Device Enrollment Manager.
"[...] If you have physical possession of the device, on an iPhone or iPad, enter the MDM Activation Lock bypass code on the Activation Lock Screen in the Apple ID password field, and leave the user name field blank. On a Mac, the bypass code can be entered by clicking Recovery Assistant in the menu bar and selecting the 'Activate with MDM key' option. Consult your MDM vendor's documentation on where to locate the bypass code."