User approved MDM
With macOS High Sierra 10.13.2, Apple introduces the concept of User Approved MDM Enrollment (UAMDM). UAMDM grants mobile device management (MDM) software additional privileges beyond what is allowed for macOS MDM enrollments that have not been “user approved”.
Third party Kernel Extensions
Currently, the benefit of UAMDM is in one area of functionality: kernel extensions. UAMDM allows an administrator to whitelist third-party kernel extensions (kext) for macOS, as well as allow or prohibit the user from enabling a kext themselves. MacOS 10.13.2 effectively disables loading third party kernel extension on devices enrolled in MDM that are not user approved.
A kernel extension can be whitelisted one of three ways, by specifying:
the team identifier that signed the kernel extension, or
the team identifier and bundle identifier of a specific kernel extension, or
or the bundle identifier of a specific un-signed kernel extension
Why does this matter?
Many software solutions, particularly in the realm of system management, security, and network connectivity (like VPN) rely on kernel extensions. If these kernel extensions are not permitted to run, the software will cease to function.
You can view the third party kernel extensions that exist on your macOS computer by running the following from terminal:
kextstat | grep -v com.apple
What makes an MDM enrollment user approved?
Note: The Apple Device Enrollment Program is now commonly referred to as “Apple Automated Enrollment Program (ADE)” and exists as part of Apple Business Manager. While some of this information in this section regarding DEP may still be relevant, we suggest that you read the aforementioned linked articles above to learn more. |
Moving forward, MDM enrollments are user approved if:
The device is enrolled using the Apple Device Enrollment Program (DEP)
The enrollment is completed interactively, by the user on the device. Enrollment using an automation, script, or even screen share will not qualify as an interactive enrollment.
As a migration path, Apple has provided an exception to this rule. Devices upgraded to 10.13.2 that are enrolled with an MDM before upgrading will be considered user approved.
If a device is enrolled with an MDM and is not user approved, the enrollment can still be elevated to user approved status. By visiting the Profiles System Preferences pane, a user will be given the option to approve the MDM enrollment and change to an approved state.
How do I whitelist Kernel Extensions with SimpleMDM?
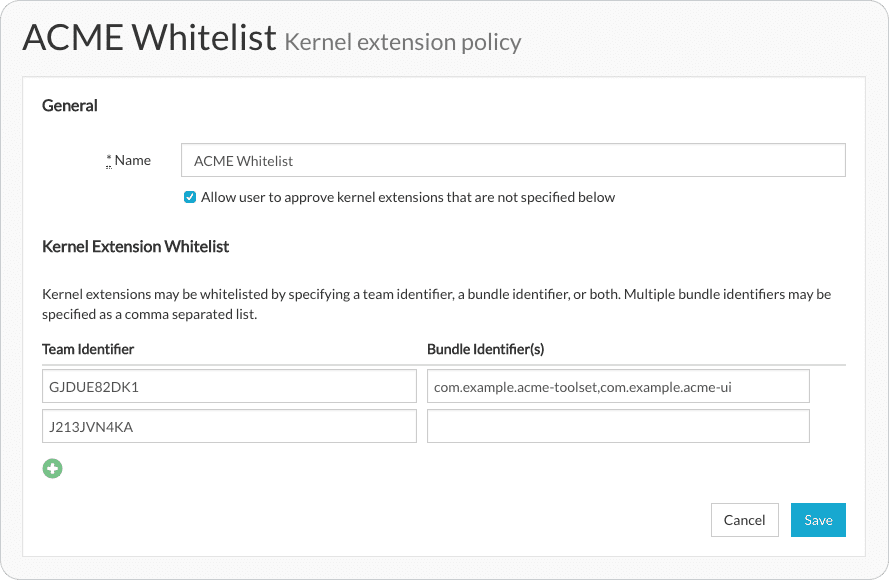
SimpleMDM allows you to define a whitelist of kernel extensions by specifying team identifiers, bundle identifiers, or a combination of the two. Users can also be permitted to approve or restricted from approving third party kernel extensions. Kernel extension policies are defined and then assigned to device groups.
Additional reading
User-Approved Kernel Extension Loading at apple.com
Prepare for changes to kernel extensions in macOS High Sierra at apple.com
Prepare your institution for macOS High Sierra at apple.com
Kernel Extensions and macOS High Sierra at derflounder.com
MDM and the Kextpocalypse 2 at richard-purves.com
User-Approved MDM Feature Request at openradar.appspot.com