Traditionally, macOS versions let applications access OS-level functionalities via Kernel Extensions. This includes resources like memory, disk access, and other hardware. While Kernel Extensions provide great functionality, they can also expose security vulnerabilities.
In macOS 10.15, Apple introduced System Extensions, which intend to replace Kernel Extensions. System Extensions provide third-party developers with access to certain system functionalities without exposing the level of vulnerabilities that kernel extensions do. Since its introduction, Apple has been encouraging developers to move toward this more modern approach.
For macOS devices running macOS 10.13 and later, Kernel Extensions must be approved by a local system administrator and whitelisted via an MDM service before they are enabled. With the release of Apple Silicon (M1) hardware devices, this process requires users to boot into recovery mode and manually reduce the security level before the apps can be run.
Implementing Kernel Extensions and System Extensions with MDM
SimpleMDM supports the ability to whitelist Kernel Extensions and System Extensions. Per Apple’s design, the Team Identifier, Bundle Identifier, or both must be specified within the definition to preapprove both Kernel Extensions and System Extensions. Here are example screenshots of both profiles for the Google Drive application:
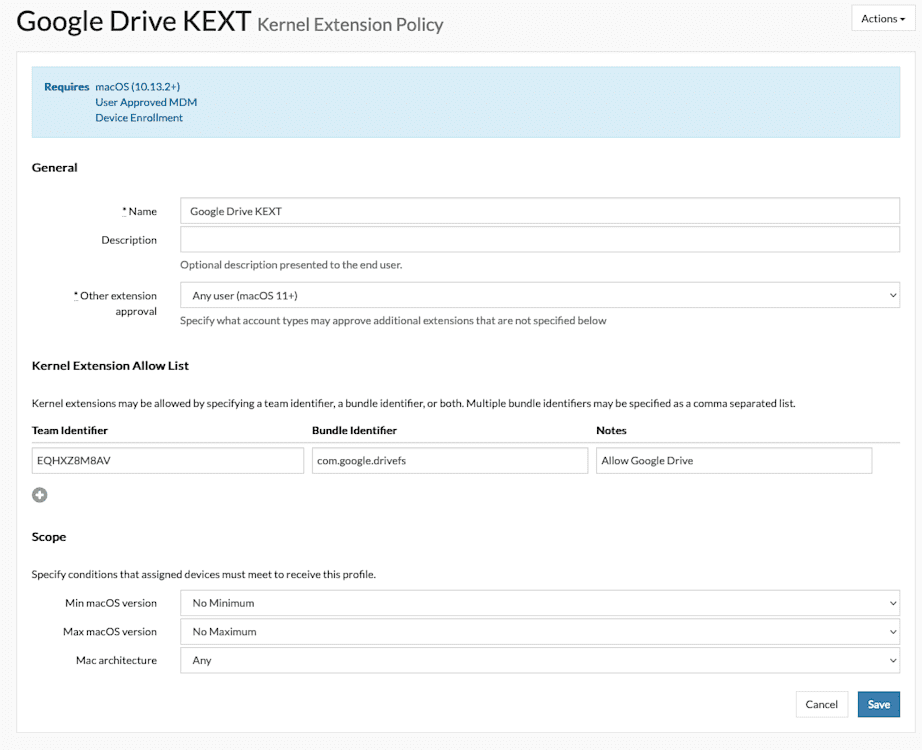
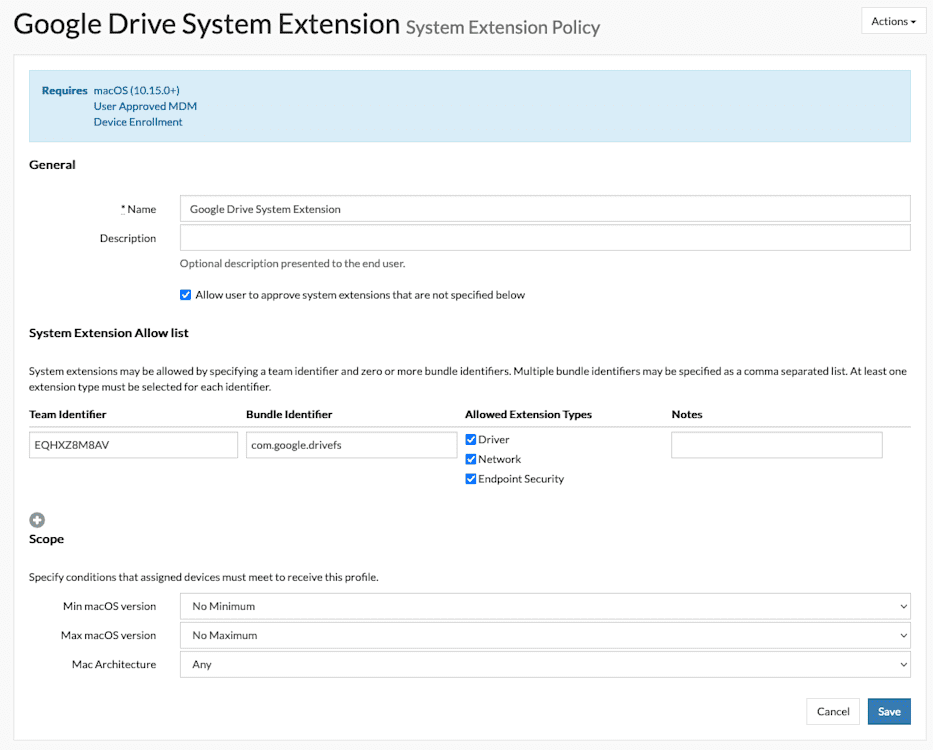
Obtaining an app’s Bundle Identifier
One method of manually obtaining the Bundle Identifier for an application requires physical access to a macOS device where the application is installed. Once installed, run the following command in terminal:
osascript -e 'id of app "[NAME OF APP]"'For Google Drive, the command would look like this:
osascript -e 'id of app "Google Drive.app"'The Mac must also install the app to obtain the Team Identifiers for Kernel Extensions. Run the following command in terminal:
sudo sqlite3 /var/db/SystemPolicyConfiguration/KextPolicy
SELECT * FROM kext_policy;This will output a list of team IDs and bundle IDs for any installed apps using them.
Activating the settings
To allow an app using Kernel Extensions to run in macOS Big Sur on a device managed with SimpleMDM, you’ll need to perform one of the following steps:
Have the user manually approve the extension within System Settings > Privacy & Security. This requires admin credentials by default. If the Kernel Extensions have been whitelisted via a profile deployed via SimpleMDM, this isn’t necessary. Suppose you have deployed the Kernel Extension Policy profile via SimpleMDM, but the app is not listed in the profile. In that case, you can set the “Other extension approval” option within the profile settings to “Any User” to allow standard users to be able to approve extensions manually without admin authentication (this is only available on macOS Big Sur and higher).
Send the Restart command to the device via SimpleMDM and set the Rebuild Kernal Cache option to Yes when sending the command.
System Extensions Policy profiles require similar information — you must include either the Team Identifier or the Bundle Identifier (or both) for any apps you want to permit. On macOS Big Sur, unlike Kernel Extensions, System Extensions only require a profile to help them; additional steps like a restart are unnecessary.