If you manage Apple devices in your organization, you’ve probably come across the term configuration profiles. But what exactly are they, how do they work, and why are they essential for mobile device management (MDM)?
In this guide, we’ll break down everything you need about configuration profiles and why they’re a cornerstone of effective device management strategies.
What is a configuration profile?
Configuration profiles are XML files that allow IT administrators to manage settings and policies on Apple devices.
MDM solutions like SimpleMDM use these profiles to configure devices remotely, ensuring they meet organizational security and operational standards.
A configuration profile is a set of instructions that tells a device how to behave, such as enforcing password requirements, configuring Wi-Fi settings, or restricting certain apps.
If you've ever seen a message on your device saying, "This setting has been configured by a profile," that's an example of a configuration profile in the wild! It means an administrator has applied a configuration profile to manage that specific setting.
As you begin deploying configuration profiles, you’ll often notice a direct correlation between the profile components and the configurable settings available in System Settings (formerly System Preferences on older operating systems). For example, in System Settings, you can upload an image to set as your wallpaper. Similarly, you can create a wallpaper configuration profile, upload an image, and deploy it to multiple devices (with supervision).
Config profiles are like Apple MDM's version of mitochondria, the powerhouse of the cell.
But perhaps you're not quite ready to be transported to ninth-grade science with me today, so let me break it down.
Why are configuration profiles important?
Configuration profiles are critical for businesses that rely on Apple devices. They enable IT teams to:
Standardize settings across devices: Ensure all devices are configured consistently.
Enhance security: Apply restrictions and policies to protect sensitive data.
Simplify management: Deploy settings remotely without manual intervention.
Save time: Automate repetitive tasks, freeing up IT resources.
How do configuration profiles work?
Configuration profiles are created and deployed through an MDM solution like SimpleMDM. Here’s how the process works:
Create the profile: Define the settings and policies you want to enforce.
Deploy the profile: Push the profile to devices via your MDM platform.
Manage the profile: Update or remove profiles as needed, ensuring devices remain compliant.
What do configuration profiles control?
With SimpleMDM, you can use configuration profiles to cater to different business requirements. These include:
1. Wi-Fi profiles: Configure access to Wi-Fi networks, including SSID, security type, and associated passwords.
2. Email profiles: Set up email accounts, including inbound and outbound servers and port numbers.
3. VPN profiles: Set up VPN configurations for secure, remote access to your organization's network.
4. Active Directory/LDAP profiles: Integrate your devices with your existing Active Directory or LDAP setups for user authentication.
5. Mobile device management (MDM) settings: Control how devices interact with your MDM. This includes security and privacy settings, software update delay settings, and MDM removal permissions.
6. Certificate profiles: Deploy private certificates for secure identification and communication.
7. iOS and macOS-specific profiles: Create custom profiles specific to the operating system. Examples include the home screen layout for iOS and FileVault settings for macOS.
8. Application configuration profiles: Set up predefined settings and data for specific device apps to assist with app management.
9. Passcode policies: Define complexity requirements, auto-lock settings, and more to ensure device security.
10. Web content filter profiles: Control access to certain websites for a safer browsing environment.
11. Device restrictions: Control access to specific features or apps, such as screen capture or app installations.
SimpleMDM has introduced Gatekeeper Policy profile support within the SimpleMDM admin interface. This profile empowers administrators to manage app security on controlled devices. It oversees Gatekeeper settings related to app installation on macOS.
SimpleMDM-supported configuration profiles
Configuration name | Allows you to define ... |
App Restrictions | an app allowlist or denylist to hide undesired apps from iOS. Requires supervision. |
AirPlay Destination | an available destination to stream audio and video. |
AirPrint Printer | an AirPrint-compatible printer for devices to use. |
APN | an Access Point Name. Also called a cellular payload. Sometimes used in advanced deployments. |
CalDAV | a WebDAV or CalDAV calendar account. |
CardDAV | a WebDAV or CardDAV contacts account. |
Certificates | deploy custom certificates to devices. |
an Exchange, IMAP, or POP-based email account. | |
FileVault | requirements around using FileVault full disk encryption. It also supports escrowing and rotating personal recovery keys. |
Firewall | Firewall settings on macOS devices. |
Firmware Password | firmware password settings and saves passwords to SimpleMDM. |
Global HTTP Proxy | an HTTP proxy that all web traffic on the device will be forced to pass through. Requires supervision. |
Google Account | a Google account to use for email, contacts, and calendaring. |
Home Screen Layout | an icon and folder layout on the iOS home screen and dock. Requires supervision. |
Kernel Extension Policy | approvals for specific kernel extensions on macOS. |
LDAP | an LDAP account typically used to populate contacts in iOS. |
Passcode Policy | complexity requirements for passcodes on iOS and macOS, as well as screen lock settings. |
Privacy Preferences | accessibility permissions for specific applications on macOS. |
Restriction | a list of iOS functionalities that should be disabled. |
Single App Lock | an app that is forced to run at all times on a device. Requires supervision. |
Single Sign-On Account | a Kerberos account to be used to sign into websites and apps. |
Software Update Policy for iOS | settings to automatically download/install iOS and tvOS updates. Requires supervision. |
Software Update Policy for macOS | settings to configure Software Update preferences and automatically download/install macOS updates. |
Subscribed Calendar | a calendar subscription. These appear in the device's calendar list. |
VPN | a VPN account, such as L2TP, PPTP, Cisco, or other popular technologies. |
Wallpaper | an image to appear in the background of the home and/or lock screen. Requires supervision. |
Web Clip | an icon on the home screen that acts as a shortcut to a website. |
Web Content Filter | a website allowlist or denylist to control web access in the Safari app. Requires supervision. |
Wireless Network | a Wi-Fi network that the device can access. |
Custom profiles can also be created based on business-specific needs using the Apple Configurator tool and imported to SimpleMDM. Thankfully, pushing Apple Configurator profiles to devices is quick and easy.
What are custom configuration profiles?
Custom configuration profiles are build-your-own profiles outside the prebuilt profiles your MDM already has for deployment (in other words, any profile not included in the table above).
How to create custom configuration profiles
My personal preference is to build a custom profile with iMazing. iMazing Profile Editor is a free macOS tool designed to help system admins manage and configure Apple devices, specifically with Apple configuration profiles. It allows users to create, edit, and sign configuration profiles.
Loading...
How to use iMazing to create mobileconfigs for MDMs
1. Download and install iMazing Profile Editor from the official website. Install the application.
2. From the desktop, double-click the iMazing Profile Editor application.

3. Create a new profile: Click File in the menu bar and select New (or press Command + N) to create a new configuration profile.
4. Add basic profile information. In the General settings, enter a profile Name and Identifier to identify the new profile uniquely.
5. Title your profile in the Name field.
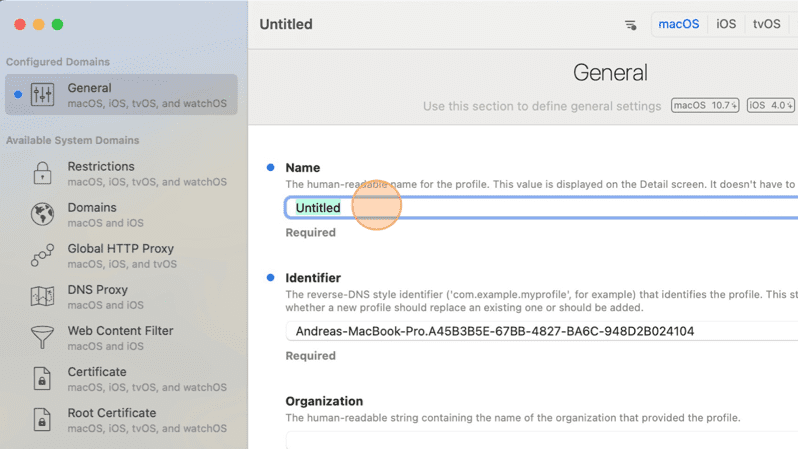
6. Fill out the Identifier field, which you can name in the com.example.myprofile fashion. (Only fields with the blue dot highlighting them are required.)
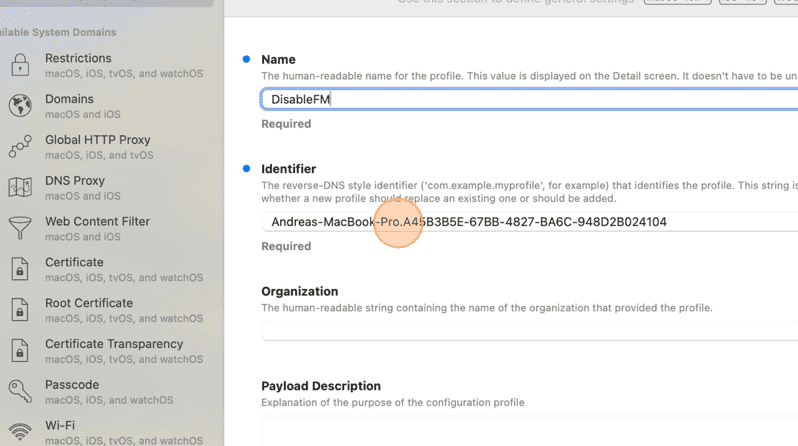
7. Scroll to the bottom of the left menu items in the iMazing application and click iCloud Find My.
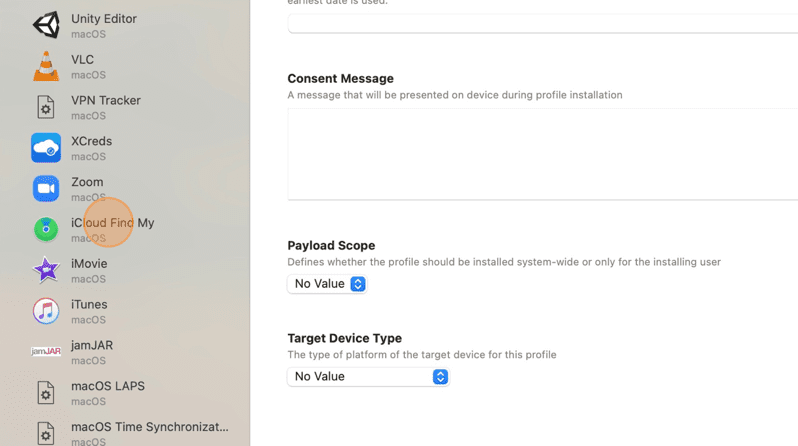
8. Click Add Configuration Payload.
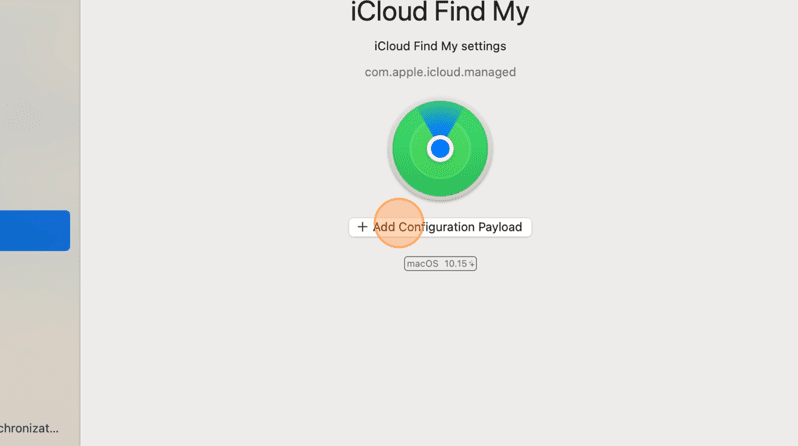
9. Click the Disable Find My iCloud Setting box to enable the payload.

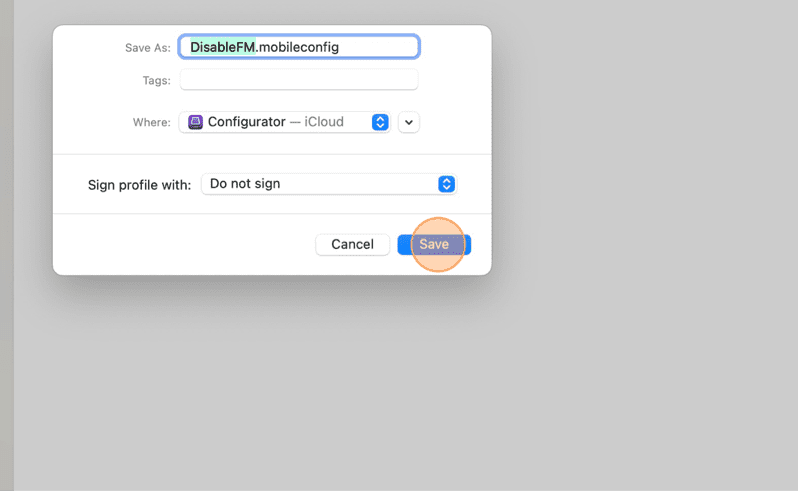
10. Press Cmd + s.
11. Click Save.
12. Open your browser and navigate to the SimpleMDM website.
13. Click Profiles.
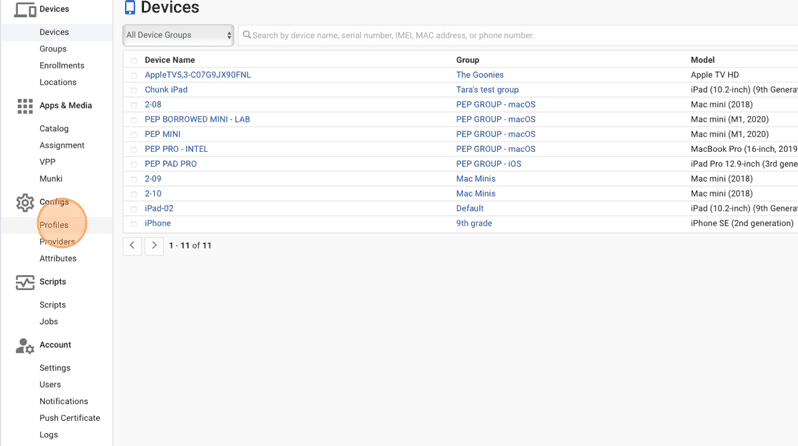
14. Click Create Profile.
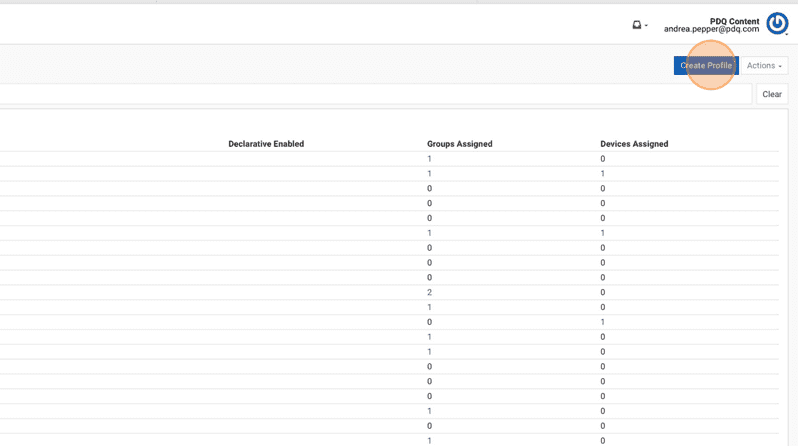
15. Click Custom Configuration Profile.
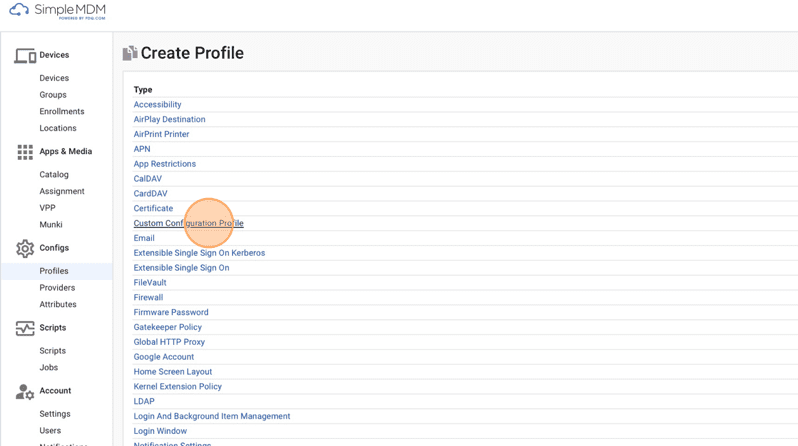
16. In the Name field, enter the name of your custom profile.
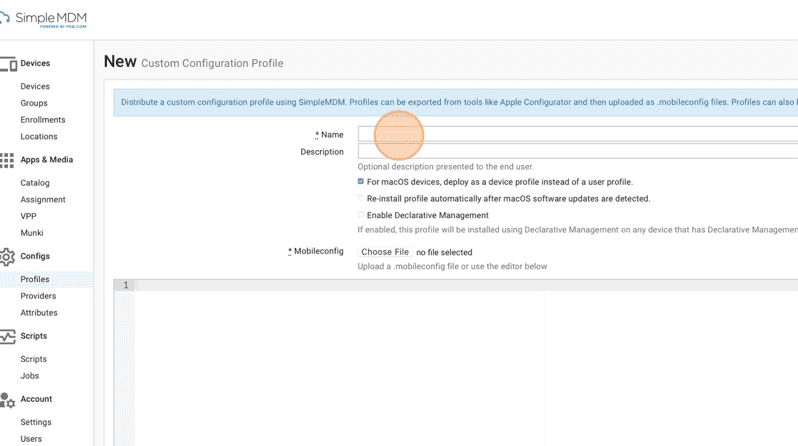
17. Type DisableFindmyMac.
18. Click Choose File to upload your iMazing config.
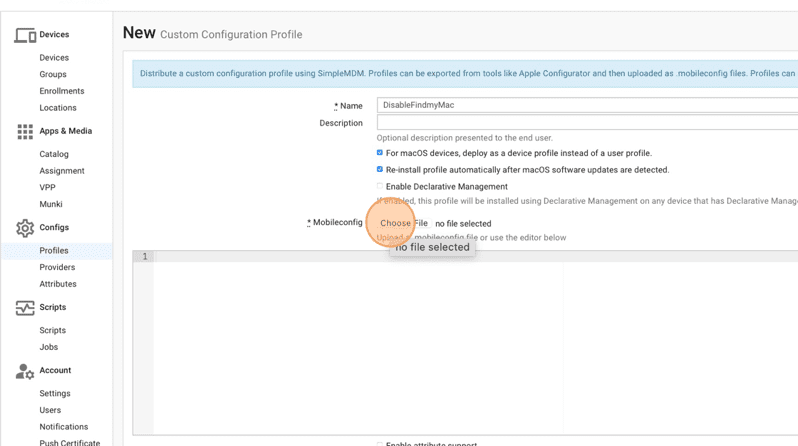
19. Click Recents.
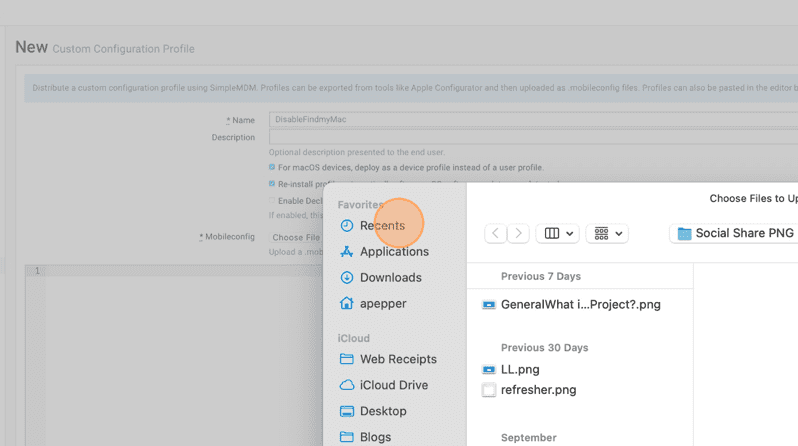
20. Click the mobileconfig you just created.
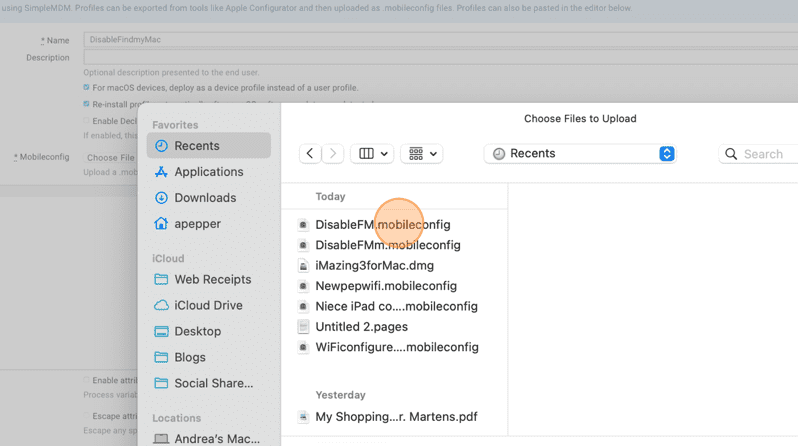
21. Click Upload.

22. Click the appropriate checkbox(es) to define your OS scope.
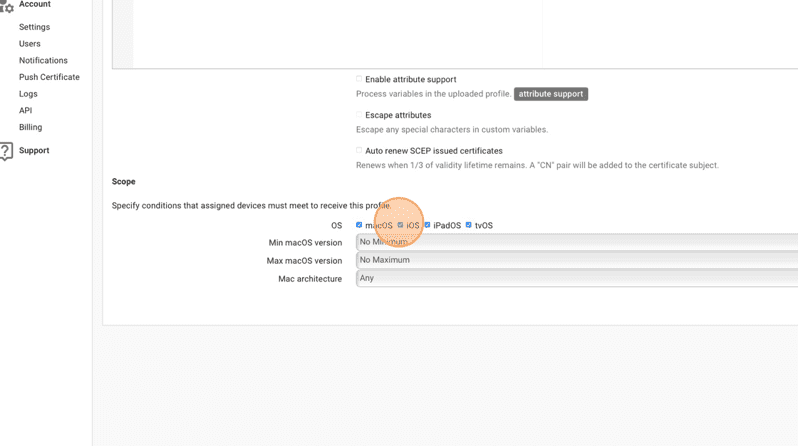
23. Click Save.
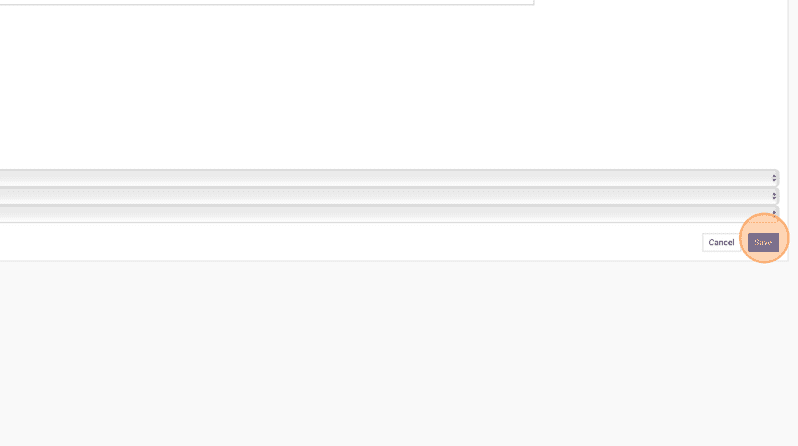
24. Click Groups.
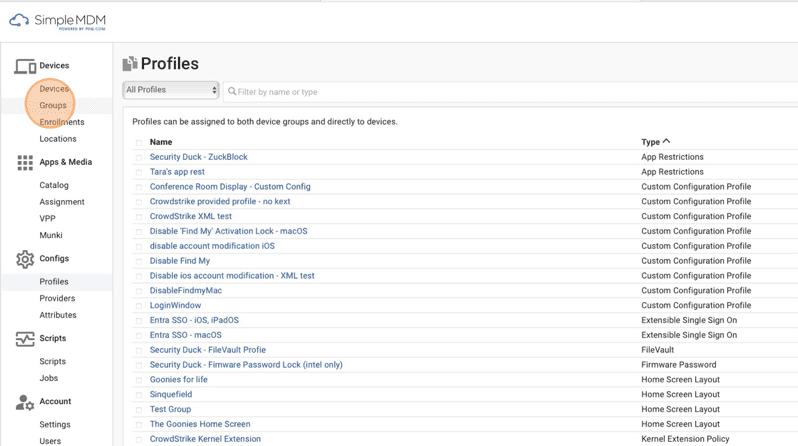
25. Click the group you'd like to deploy your profile to.
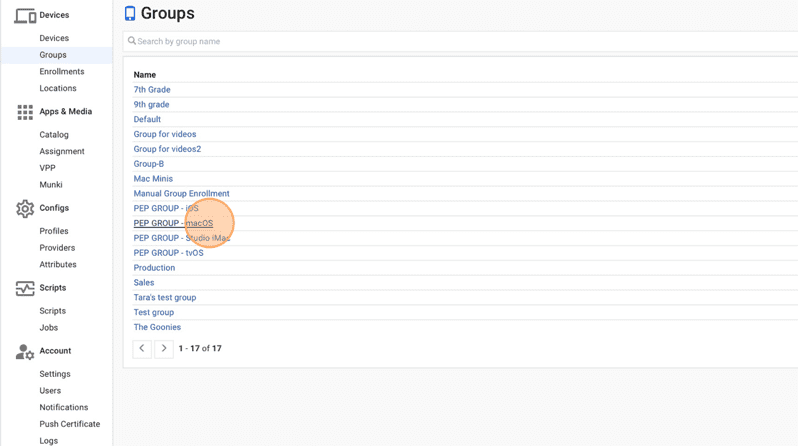
26. Click Profiles.
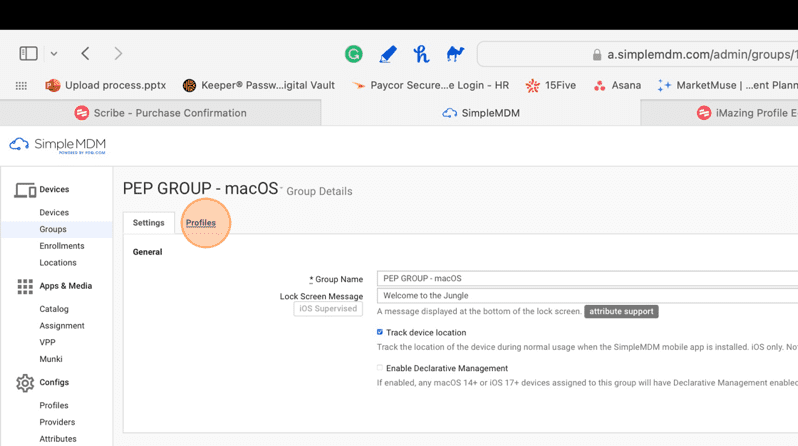
27. Click Assign Profile.
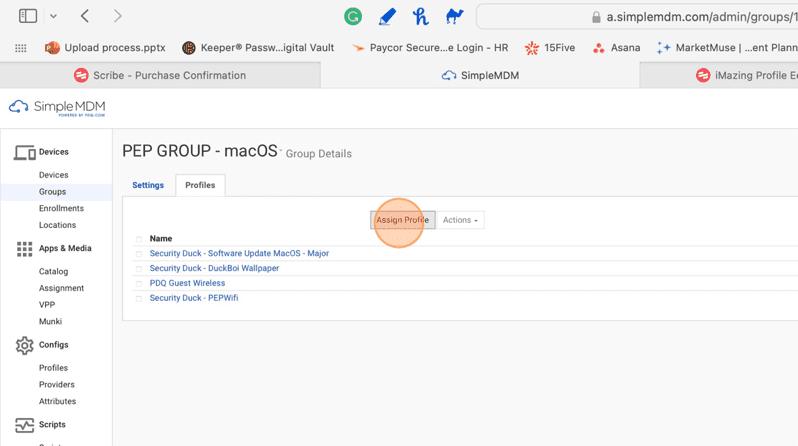
28. Under Assign Profile, click the Filter by name or type the profile name in the text field.
29. Click Assign.
Click through the video instructions here:
Loading...
Our favorite custom configuration profiles
Here are a few custom config profiles you can try out yourself!
1. Conference Room Display (tvOS)
Supervision required
This is one of my favorite configuration profiles, and honestly, Apple TV for enterprise is slept on when you consider features like this!
Conference Room Display mode for Apple TV transforms Apple TV into a SAM-type locked conference room display. It prevents tampering and enables simple screen sharing via AirPlay from Mac, iOS, or iPadOS devices.
Once activated, the TV display defaults to displaying AirPlay instructions and wireless network details and remains unmodifiable. In addition, the customizable screen allows organizations to configure the display's branding and messaging to match their corporate identity.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>Message</key>
<string>Please use Airplay to stream media from your device. </string>
<key>PayloadDisplayName</key>
<string>Conference Room Display</string>
<key>PayloadIdentifier</key>
<string>com.apple.conferenceroomdisplay.82C0F5D6-4C8D-4D63-9F93-F9BFD1B8C47B</string>
<key>PayloadType</key>
<string>com.apple.conferenceroomdisplay</string>
<key>PayloadUUID</key>
<string>82C0F5D6-4C8D-4D63-9F93-F9BFD1B8C47B</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</array>
<key>PayloadDisplayName</key>
<string>Conference Room Display</string>
<key>PayloadIdentifier</key>
<string>com.conferenceroom.profile</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>1D06C6F8-0680-4D6F-A787-83939CF52983</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>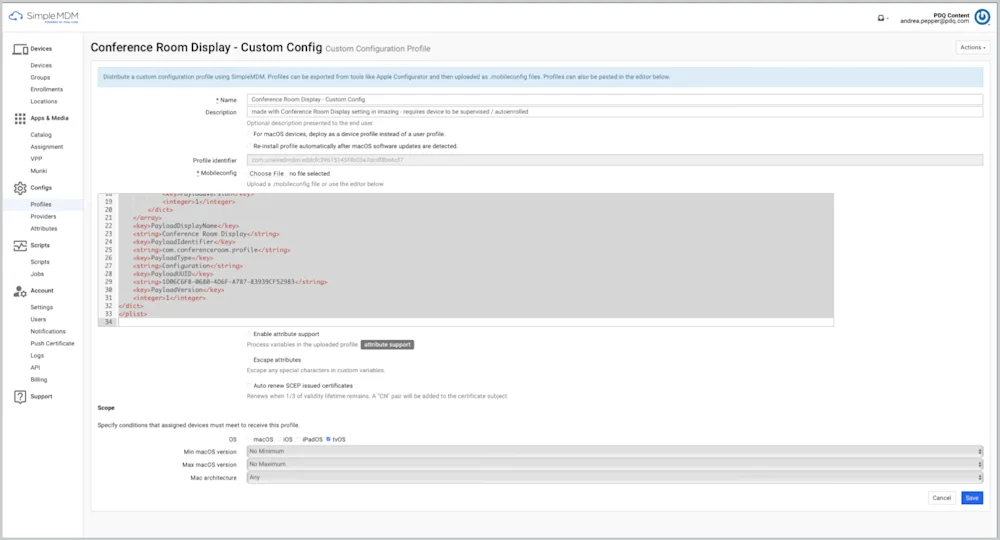
Note: This profile is tvOS only, so check the box for tvOS when deploying this profile!
2. Disable Find My Activation Lock [macOS]
Another favorite macOS custom configuration profile is this nifty restriction for disabling "Find My" on macOS. Check out in-depth instructions on how to manage Activation Lock for enterprise environments.
Loading...
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDisplayName</key>
<string>Restrictions</string>
<key>PayloadIdentifier</key>
<string>com.apple.applicationaccess.67A8AB6B-A67B-4193-8681-FA78886B143D</string>
<key>PayloadType</key>
<string>com.apple.applicationaccess</string>
<key>PayloadUUID</key>
<string>67A8AB6B-A67B-4193-8681-FA78886B143D</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>allowAccountModification</key>
<false/>
<key>allowFindMyDevice</key>
<false/>
<key>allowFindMyFriends</key>
<false/>
</dict>
</array>
<key>PayloadDescription</key>
<string>ios account settings restriction profile not managable </string>
<key>PayloadDisplayName</key>
<string>Disable modification of IOS account settings </string>
<key>PayloadIdentifier</key>
<string>com.accountsettingsmodify.disabled</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>E08E9953-CA91-4924-9F85-8D90CFAE9C41</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>3. Choose your own adventure!
From Zoom to Chrome, CrowdStrike, or Office, the whole point of custom configurations is endless possibilities!
Research the parameters for configuration profiles.
Mix and match prebuilt configurations.
See what other profiles MacAdmins create!
Our favorite configuration profiles
By operating system
We know you want to keep your profile deployment time to a minimum (so you can keep your beer time to a maximum). SMDM has already prebuilt all the super handy ones for you!
Here are a few notable options that you can try out this week:
macOS
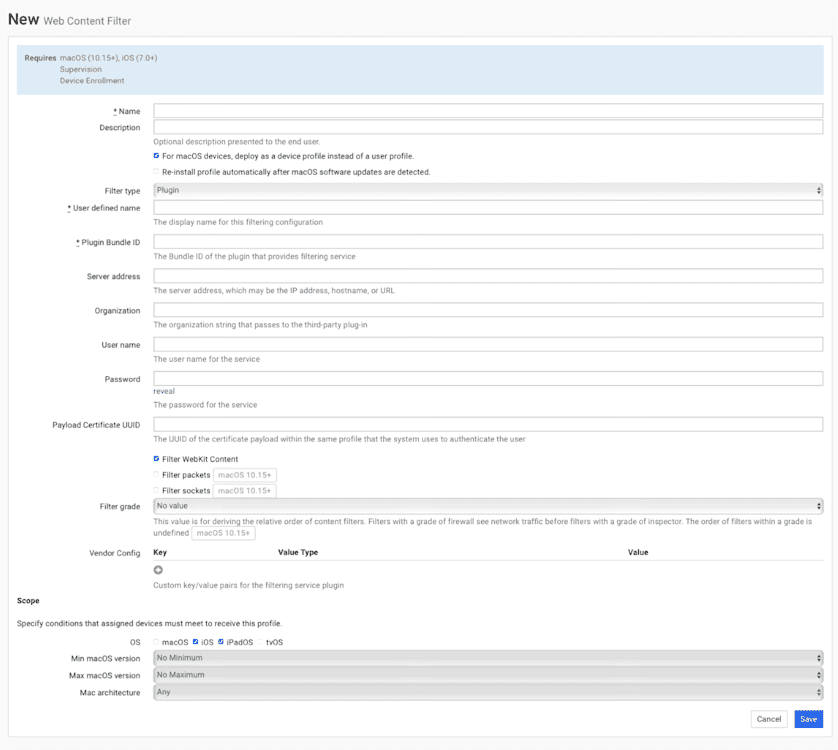
Web Content Filter
Supervision required
A Web Content Filter profile is a configuration profile applied to devices to manage and control access to specific web content. When a Web Content Filter profile is applied to a device, it can limit or block access to specific websites or categories based on predefined rules or settings. This helps prevent users from accessing inappropriate, unsafe, or unproductive content while using the device.
iOS
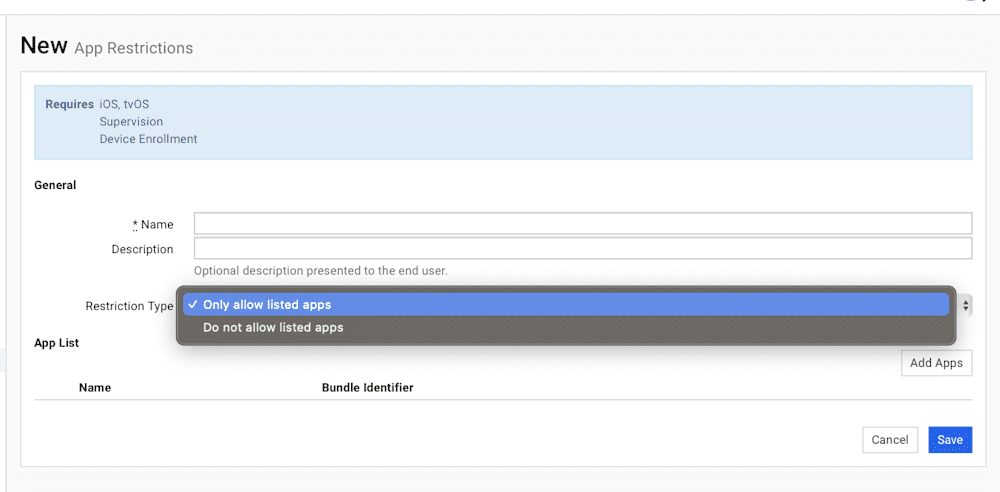
App Restrictions
Supervision required
The App Restrictions profile is exactly what it sounds like. This profile allows you to create an allowlist or a denylist for iOS devices and add applications to that list by searching the App Store or bundle ID.
iPadOS
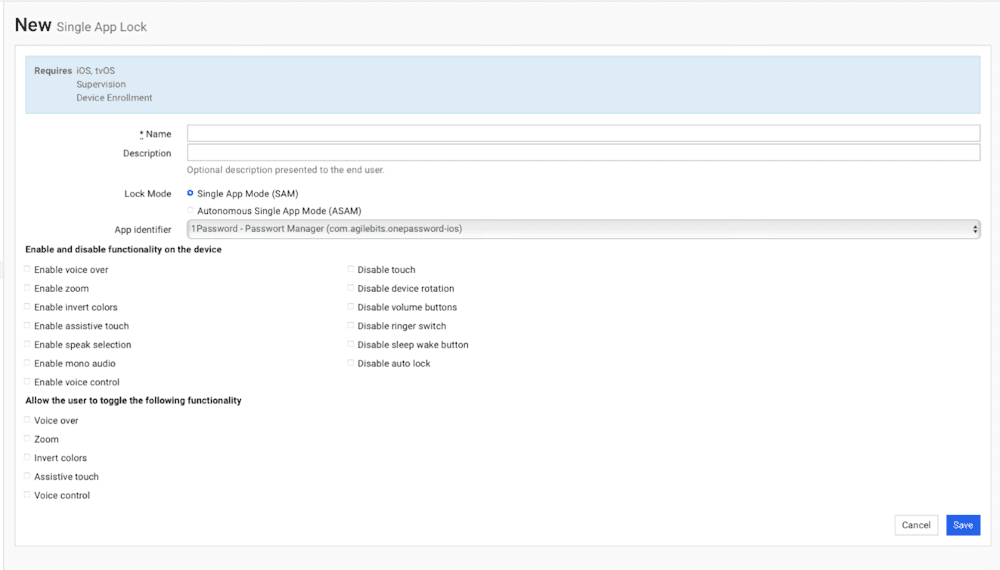
Single App Lock
Supervision required
To no one's surprise, my go-to profile favorite for iPads will always be Single App Lock. Our in-depth article discusses how to utilize this profile to create Kiosk devices.
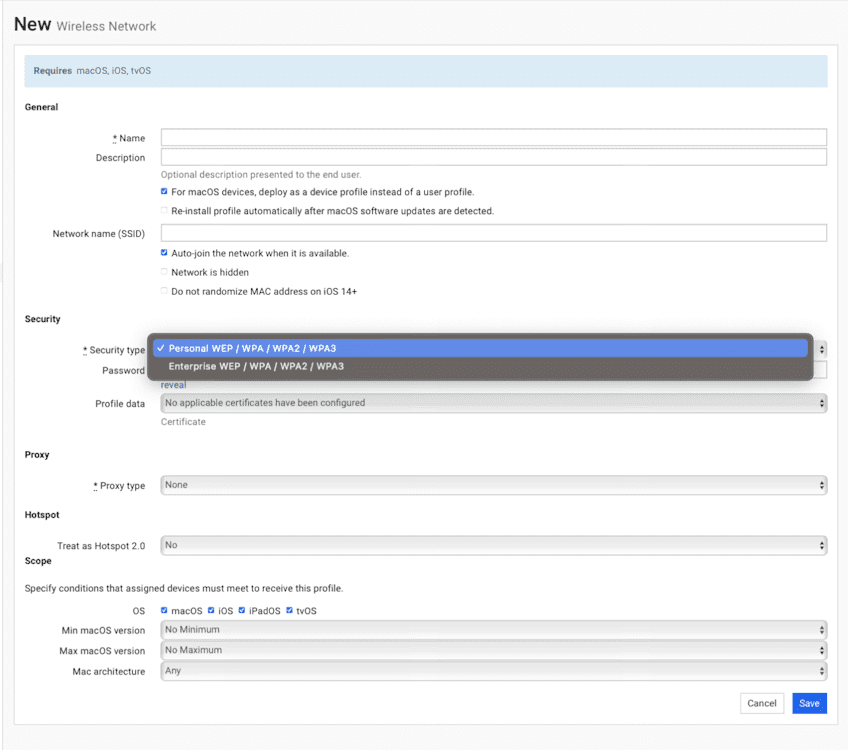
Overall winner
Wireless Network
This one is a no-brainer! This profile is the first profile you need on each device and the last one you'll ever take off. Unlike most profiles, it's compatible with every OS (macOS, iOS, iPadOS, tvOS) and doesn't require supervision. This profile lets you quickly customize and deploy a preconfigured Wi-Fi network to any device. It's about the most standard profile you can create, but classics are classic for a reason.
SimpleMDM added support for Apple's Printing profile in the SimpleMDM admin interface. This profile enables Administrators to configure printing settings and preferences on macOS devices. It manages printing preferences, like default printers, quotas, job permissions, and user group access.
Configuration profile context information
Attributes of configuration profiles
A configuration profile is an XML-based .plist file comprising several components, including the:
Payload identifier
Organization identity
Payload type
Description
Scope
Version
The payload content is a critical component, containing the specific settings and commands the profile will enforce or apply.
payload content = the part that has the stuff that does the things
What is XML?
XML, or Extensible Markup Language, establishes rules for encoding documents in a format intuitive to humans and computers alike. Allowing custom tagging schemes fosters document diversity while delivering a perfect balance of readability and flexibility for data storage and transmission.
What is property list (.plist)?
PLIST, a shortened term for property list, is a data file used across macOS to store user preferences and application data. These files serialize objects like numbers or strings and typically utilize XML or binary formats. When written in XML, .plist files use this language as a "vessel" for structuring and storing data.
In short, .plist is the nature of the data file, and XML is the format that structures that data.
Okay, so configuration profiles are XML written in .plist format. Cool, I feel smart.
PLIST is the data format, XML is the markup language used for constructing the data, and configuration profiles apply these technologies to manage settings on Apple devices. It's like getting from A to B: PLIST defines the car, XML is the roadmap, and configuration profiles are the destination.
Configuration profile keys
Configuration profile keys encompass those within a configuration profile, including payload dictionary keys and payload-specific property keys. They may also refer to top-level keys defining the profile structure. For instance, PayloadDisplayName and PayloadRemovalDisallowed set the profile's name and removal permission, respectively.
Each payload contains a set collection of configuration profile keys within the configuration profile, stipulating a device's enforced settings or configurations. The values are set and encoded into a profile, which takes effect when installed.
You keep mentioning payloads …
The configuration profile XML's core content or payload contains managed devices' settings, restrictions, and rules. Each payload has payload-specific keys denoting key settings.
Payload dictionary keys
Every configuration profile contains payloads and dictionaries of key-value pairs. Payload dictionary keys constitute the main payload properties, conveying essential information: PayloadType, PayloadVersion, PayloadIdentifier, and PayloadUUID, for example.
Payload-specific property keys
These apply specifically to individual payloads. Unique to their payload type, they determine actual settings or configurations, like a Wi-Fi payload specifying SSID and password.
Think of configuration profiles as books:
Configuration profile keys are chapters.
Payload dictionary keys serve as chapter titles.
Payload-specific property keys are the detailed content within.
Config profile FAQs
What are config profiles?
Config profiles are the same as configuration profiles. Configuration profiles are XML files containing settings and restrictions that can be applied remotely to Apple devices managed by an MDM server.
How do I create custom configuration profiles in SimpleMDM?
You can create custom configuration profiles in SimpleMDM by following these steps:
Loading...
Obtain your XML payload:
Create an XML, copy an existing XML, or configure a custom XML using a tool like iMazing.
Add the Profile in SimpleMDM: Go to Profiles > Create Profile> Custom Configuration Profile. Name the profile.
Add the .mobileconfig:
Click Choose File and upload the .mobileconfig from your computer.
Or, paste the code into the text editor field.
Review the two boxes below the text editor:
For macOS devices, deploy as a device profile... — Check this box for default device-level deployment.
Enable attribute support — Leave unchecked unless using custom attributes.
Save the profile:
An error message will appear if there's an issue and prevent you from saving the profile.
Deploy the profile:
Assign the profile to your device groups by checking the box next to the profile name on the Device Group Details page.
Still have questions? Please read our instructions on building a custom configuration profile from scratch and review the latest documentation for accurate and up-to-date steps.
How else can I deploy configuration profiles outside of MDM?
Configuration profiles can be deployed through various methods outside MDM, including:
Using Apple Configurator 2: You can utilize Apple Configurator 2, accessible on the App Store.
Via email
On a webpage
Over-the-air configuration: Employ the over-the-air profile delivery and configuration method detailed in Over-the-Air Profile Delivery and Configuration.
Ready to maximize your Mac management? From education to enterprise deployments, SimpleMDM is ready to go!